AWS Secrets Manager
With this integration you can store, manage, and retrieve, secrets in Amazon Web Services Secrets Manager.
Official Websitehttps://aws.amazon.com/secrets-manager/
TagsSecretsRotationSaas
JavaScript
Python
Documentationhttps://docs.aws.amazon.com/AWSJavaScriptSDK/v3/latest/clients/client-secrets-manager/index.html
Version3.316.0
Documentationhttps://boto3.amazonaws.com/v1/documentation/api/latest/reference/services/secretsmanager.html
Pypi packagehttps://pypi.org/project/boto3/
Version1.34.23
Source Codehttps://github.com/boto/boto3
Credential configuration
To configure this credential, you need the Access Key Id and the Secret Access Key of the Programatic access
user you want to use. Make sure this user has the required permissions
to access Secrets Manager to work properly. If you need to create the user,
follow the instructions provided here.
In the extra options field, you can include any of the parameters you can find here.
Here is an example of a filled credential configuration form in YepCode:
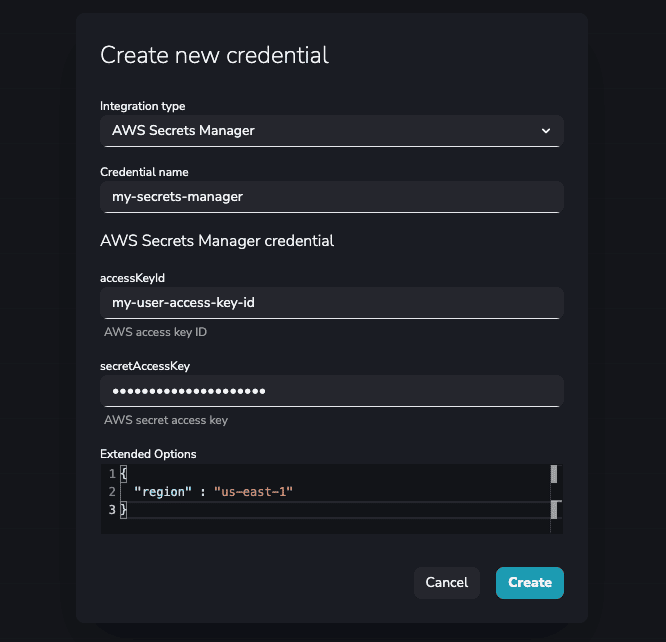
AWS Secrets Manager Snippets available in YepCode editor
note
The title is the triggering text for YepCode to autocomplete the script.
JavaScript
Python
Integration
New integration from credential
const awsSecretsManagerClient = yepcode.integration.awsSecretsManager("credential-slug");
New integration from plain authentication data
const { SecretsManagerClient } = require("@aws-sdk/client-secrets-manager");
const awsSecretsManagerClient = new SecretsManagerClient({
credentials: {
accessKeyId: "accessKeyId",
secretAccessKey: "secretAccessKey",
},
});
Create Secret
Create secret
const { CreateSecretCommand } = require("@aws-sdk/client-secrets-manager");
const createSecretCommand = new CreateSecretCommand({
Name: "secret-name",
SecretString: "secret-to-store",
});
awsSecretsManagerClient.send(createSecretCommand).then((response) => {
console.log(`Created secret with name ${response.Name}`);
}).catch(console.error);
List Secrets
List secrets
const { ListSecretsCommand } = require("@aws-sdk/client-secrets-manager");
const listSecretsCommand = new ListSecretsCommand({});
awsSecretsManagerClient.send(listSecretsCommand).then((response) => {
const secrets = response.SecretList;
secrets.forEach((secret) => console.log(`Found secret with name ${secret.Name}`));
}).catch(console.error);
Get Secret Value
Get secret value
const { GetSecretValueCommand } = require("@aws-sdk/client-secrets-manager");
const getSecretValueCommand = new GetSecretValueCommand({
SecretId: "secret-name-or-ARN"
});
awsSecretsManagerClient.send(getSecretValueCommand).then((response) => {
// Secret value comes in response.SecretString or response.SecretBinary
// If you store other types of secrets different than key value pairs,
// then it will come as a JSON string
}).catch(console.error);
Delete Secret
Delete secret
const { DeleteSecretCommand } = require("@aws-sdk/client-secrets-manager");
const deleteSecretCommand = new DeleteSecretCommand({
SecretId: "secret-name-or-ARN"
});
awsSecretsManagerClient.send(deleteSecretCommand).then((response) => {
console.log(`Deleted secret with name ${response.Name}`);
}).catch(console.error);
Integration
New integration from credential
aws_secrets_manager_client = yepcode.integration.aws_secrets_manager("credential-slug")
New integration from plain authentication data
import boto3
session = boto3.Session(
aws_access_key_id="accessKeyId",
aws_secret_access_key="secretAccessKey",
region_name="region"
)
aws_secrets_manager_client = session.client("secretsmanager")
Create Secret
Create secret
aws_secrets_manager_client.create_secret(
Name="secret-name",
SecretString="secret-value-to-store"
)
List Secrets
List secrets
response = aws_secrets_manager_client.list_secrets()
secrets = response['SecretList']
for secret in secrets:
print(f"Found secret with name {secret['Name']}")
Get Secret Value
Get secret value
response = aws_secrets_manager_client.get_secret_value(
SecretId="secret-name-or-ARN"
)
# Secret value comes in response.SecretString or response.SecretBinary
# If you store other types of secrets different than key value pairs,
# then it will come as a JSON string
Delete Secret
Delete secret
aws_secrets_manager_client.delete_secret(
SecretId="secret-name-or-ARN",
ForceDeleteWithoutRecovery=True
)